Cyber Self-Defense
January 5, 2019
Every other week there’s a news story about a data breach where millions of people have had credit card numbers, social security numbers, email address or passwords leaked out onto the internet. As an example, between May and July 2017, Equifax had a data breach that according to the Federal Trade Commission exposed the “names, Social Security numbers, birth dates, addresses and, in some instances, driver’s license numbers” of somewhere around 143 million Americans. That’s about 50% of the population. So if the giant companies can’t keep your data safe, how can you possibly do it?
While you have no control over the data in their systems, there are a few simple steps you can take to keep unauthorized individuals out of your email, social media, banking, and other online accounts. These steps fall into two basic categories:
- Don’t get phished
- Be difficult to hack
Phishing vs. Hacking
Depending on who you ask, you’ll get different definitions, but in my opinion, phishing (pronounced “fishing”) is the act in which an attacker poses as a trustworthy individual or institution and tricks the victim into simply handing over their username and password. Hacking, on the other hand, is the act in which an attacker gains access to the victims accounts or data by guessing their password, exploiting security flaws, or otherwise breaking through the barriers in place. A simple analogy is that phishing is tricking someone into thinking that they’re the valet and stealing the car while hacking is picking the lock, breaking the window, or towing the car away to your chopshop.
So how can I avoid being phished?
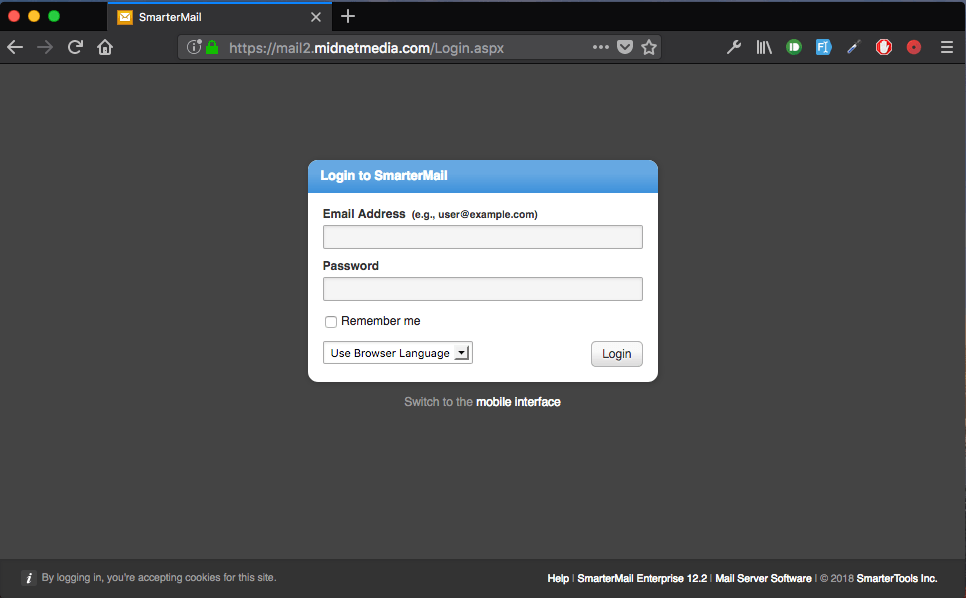
Everywhere you go online now they want you to log in. Email, social media, online shopping, e-banking, and all sorts of other sites make you sign in before you can see your account, and you’ll usually see a page structured like this:
Login window at
midnetmedia.com
You’ve got a spot for a username and a spot for a password. That’s a simple site to build for someone with nefarious intentions. All they have to do is send you an email with a fake link (again, very easy, check out this link to https://www.gmail.com) and then you type your information in and that’s it, they know your login information.
This happens all the time. They might send you a message pretending to be Amazon saying your recent purchase failed and that you need to update your payment information. They might pretend to be Facebook and want you to login to approve a phony friend request.
There is, however, a way to tell if your link is legitimate. Let’s zoom in to the address bar.
Firefox's address bar displays a green lock icon and the https:// protocol when connected securely.
Chrome's address bar displays a green lock icon, the word "secure", and the https:// protocol when connected securely.
Safari's address bar displays a lock icon connected securely. Clicking on the URL also reveals the https:// protocol.
Your browser will tell you what site you’re logging into in the address bar at the top of the page. If the attacker’s email said it was going to Gmail and then goes somewhere else, your browser will always tell you the truth. Another thing to look for is if your browser shows the site as “http://” or “https://” That “s” stands for “secure” and means that whoever is running this site has an SSL certificate
proving to your browser who they are. If your browser loads a site starting with “https://” and you recognize the web address, you can be pretty certain you’re at the real version of the site you’re logging into.
This is the most convincing way to phish, but there are others that are worth mentioning. The classic “Nigerian Prince” email is a 21st century version of an advance-fee scam
where someone promises you large sums of money, all they need is your bank account information so they can deposit it. Another is the annual IRS phone scam
that you’ll likely hear about as tax season approaches. If you’re concerned if something is a phishing attempt, your best bet is to attempt to verify the information, either through a phone call, or by going to the recommended site without clicking any links you were sent in the questionable emails.
And how can I avoid being hacked?
While in phishing attacks you can be more vigilant and skeptical of questionable sources, hacking attacks aren’t always detectable until it’s too late, so your best bet is to make yourself a more difficult target.
The first step to making yourself less of a target is having a good password. There are lots of different thoughts on how to make the strongest password, but there is some consensus on what makes the worst passwords. If you see your password on this list, we highly recommend changing it today.
To get an idea of how to make a strong password, it’s good practice to think about how passwords can be broken, which generally falls into two categories:
- Guessing personal information (birthdays, anniversaries, kids’ names, etc) Using significant dates and names as a password makes it very easy for you to remember your password, but it also drastically reduces the number of options an attacker has to go through to guess the correct password.
- Brute force trial-and-error Initially with brute force attacks, an attacker uses a computer to loop through all possible combinations of letters to break a password, and so security professionals recommended longer passwords made up of a few easy-to-remember words so the computers guessing would statistically have to go through trillions of trials before stumbling upon your password, but then attackers adapted to attempt combinations of words, making your 5-word password no better than a 5-letter password.
The strongest passwords of today all have a few things in common:
- Length
- Mixed case
- Add numbers
- Add symbols
- Avoid personal information
- Avoid reusing passwords
That last tip is a big one. Like we mentioned earlier, data breaches are just another part of 21st century life now, and part of that is your email address and passwords for those sites being exposed. If you log in with the same password across all your sites and your password is ever exposed, suddenly all your other accounts become vulnerable. Keeping a strong password unique to each account is the best way to keep all of your various accounts secure. If you’re worried about forgetting dozens of different passwords, fear not, here are a few password manager services
that will help you keep all your accounts locked up tight.
The second step to making yourself less of a target is to make sure the only way to access your information is through the login page. You’ve likely seen these icons or messages on your computer or website.
Keeping your computers, websites, and other accounts consistently up-to-date is the best way to keep people from exploiting weaknesses in the programs that normally keep them out. Just this past September, Apple launched the newest iteration of their operating system, OS 10.13 “High Sierra”, and in November, it was found to have a major security flaw
where anyone could log into the computer with the username “root” and no password. At that point, it doesn’t matter how strong, complex, or unique your password is, because attackers can just go around it.

Effective Social Media Strategies for Engaging Audiences In today's digital landscape, social media has become a cornerstone for businesses and organizations looking to connect with their audiences. With billions of users active on platforms like Facebook, Instagram, Twitter, and LinkedIn, the potential for engagement is immense. However, with this potential comes the challenge of standing out in a crowded space. Here are some effective social media strategies to help you engage your audience meaningfully and maximize your online presence. 1. Define Your Target Audience Understanding who your audience is crucial for crafting content that resonates. Develop detailed buyer personas by considering demographics, interests, and online behaviors. This knowledge will guide your content creation, ensuring it addresses the needs and preferences of your audience. 2. Create Valuable and Shareable Content Content is king, but it must be valuable to your audience. Aim to provide insights, entertainment, or solutions to problems they face. Use a mix of formats—videos, infographics, blogs, and images—to cater to different preferences. Don’t forget to encourage sharing by creating content that’s easily shareable, such as listicles, how-tos, and inspirational quotes. 3. Leverage Storytelling Humans are wired to connect through stories. Share your brand’s story, customer testimonials, or case studies to create emotional connections. Authentic storytelling can foster trust and loyalty, making your audience feel like they are part of your journey. 4. Engage with Your Audience Social media is a two-way street. Respond to comments, messages, and mentions promptly. Ask questions and encourage discussions to foster a sense of community. Use polls and surveys to invite feedback, showing that you value your audience’s opinions. 5. Utilize Hashtags Strategically Hashtags can expand your reach and visibility. Research relevant hashtags in your industry and create branded hashtags to build community around your content. Don’t overdo it; a few well-chosen hashtags are often more effective than a long list. 6. Post Consistently and at Optimal Times Consistency is key to keeping your audience engaged. Develop a content calendar to plan your posts and maintain a regular schedule. Use analytics tools to identify when your audience is most active and schedule your posts accordingly to maximize visibility. 7. Monitor and Analyze Performance Regularly analyze your social media metrics to understand what’s working and what isn’t. Track engagement rates, reach, and audience growth. Use this data to refine your strategies and focus on content types and topics that resonate best with your audience. 8. Collaborate with Influencers Influencer marketing can be an effective way to reach new audiences. Collaborate with influencers whose values align with your brand to amplify your message. This can introduce your brand to their followers and build credibility through trusted voices. 9. Utilize Paid Advertising Organic reach can be limited, especially on platforms like Facebook. Consider investing in paid advertising to boost your posts and target specific demographics. Use A/B testing to optimize your ads and ensure you’re getting the best return on investment. 10. Stay Authentic and Transparent In an era where consumers value authenticity, being transparent about your practices and values can set you apart. Share behind-the-scenes content, company culture, and challenges you face. This openness can deepen the trust and connection between you and your audience. Conclusion Implementing effective social media strategies can significantly enhance your ability to engage and connect with your audience. By understanding their needs, creating valuable content, and fostering genuine interactions, you can build a loyal community around your brand. Remember, social media is not just about promotion; it’s about creating relationships that matter. Embrace these best practices to maximize your social media presence and watch your engagement soar!

Case Study: The Rise of Minster Oktoberfest's Online Presence As our community puts a bow on this year's Minster Oktoberfest, we wanted to take a moment to highlight a fascinating case study on the website, minsteroktoberfest.com. Tracking its traffic leading up to the event reveals valuable insights into digital engagement and the effectiveness of event marketing. A Closer Look at the Numbers In the 30 days surrounding Minster Oktoberfest, the website experienced a significant surge in visits. Here’s a breakdown of the impressive stats: Total Visits: The site garnered 33.6k visits in the month leading up to the event. Early September Activity: Around September 1st, the site had a modest average of 500 views per day. End of September Surge: By the end of September, daily views jumped to an average of 1,600, signaling growing interest. Peak Traffic: During the prime days of Oktoberfest week/weekend, daily views soared to an impressive 6,000. Mobile vs. Desktop Growth The increase in traffic wasn’t just notable in total visits; it also highlighted a shift in how users accessed the site: Mobile Visits: There was a staggering 378.7% increase in mobile visits, reflecting the growing trend of users accessing information on their phones. Desktop Visits: Desktop visits also saw significant growth, up by 251.7%, showcasing that both platforms are important for engaging audiences. What Contributed to the Surge? Several factors likely contributed to this dramatic increase in website traffic: 1. Effective Marketing Campaigns: As event promotions ramped up, marketing efforts across social media, email newsletters, and local advertising likely drove more traffic to the site. 2. Engaging Content: Regular updates, engaging content, and event highlights may have kept potential attendees returning to the site for more information. 3. User-Friendly Design: A well-structured website that provides easy navigation and accessibility encourages visitors to explore more and share with others. 4. Community Engagement: As a community-focused event, local engagement and word-of-mouth likely played a significant role in boosting online interest. Conclusion The case of minsteroktoberfest.com serves as an excellent example of how effective digital strategies can significantly enhance engagement leading up to a major event. Tracking these trends not only showcases the event's popularity but also emphasizes the importance of a strong online presence for cultural events. As we continue to be involved with projects like this, we’re excited to see how digital engagement will evolve in the future. If your organization is looking to enhance its online footprint, let’s connect and explore the possibilities together!

Transforming Digital Experiences: Armstrong Air & Space Museum's Website At Midnet Media, we believe that a strong online presence is crucial for cultural institutions to connect with their communities and share their stories. That's why we are excited to showcase our latest project: the newly revamped website for the Armstrong Air & Space Museum. This partnership not only highlights our commitment to enhancing digital experiences but also underscores the importance of making history accessible to everyone. A Fresh Look for a Rich History The Armstrong Air & Space Museum, dedicated to preserving and celebrating the life of the legendary astronaut Neil Armstrong, needed a website that reflected its rich heritage while being user-friendly and visually appealing. Our goal was to create a digital space that invites visitors to explore Armstrong's incredible journey from small-town Ohio to the moon. Key Features of the New Website 1. **User-Centric Design** We prioritized an intuitive layout that allows visitors to easily navigate through various sections, including exhibits, educational resources, and event information. The design incorporates visually engaging elements that draw users in while providing a seamless browsing experience. 2. **Responsive and Accessible** With more people accessing websites from mobile devices, we ensured the Armstrong Air & Space Museum's site is fully responsive. Our team implemented accessibility features to ensure that everyone can enjoy the content and resources available. 3. **Interactive Exhibits** One of the standout features of the new site is the interactive exhibits section. Users can explore Neil Armstrong's life through engaging multimedia presentations, videos, and photographs that bring his story to life. 4. **Event Calendar** The museum hosts a variety of events throughout the year, from lectures to community gatherings. Our integrated event calendar makes it easy for visitors to stay informed and participate in the museum’s offerings. Collaboration and Feedback Working closely with the team at the Armstrong Air & Space Museum was a rewarding experience. Their passion for education and community engagement inspired our design choices and content strategies. Throughout the development process, we prioritized open communication and feedback, ensuring that the final product truly reflects the museum's mission. The Impact of the New Website Since the launch of the new Armstrong Museum website, early feedback has been overwhelmingly positive. Visitors appreciate the modern aesthetic and ease of navigation, and the museum staff is excited about the increased engagement and accessibility. This project has not only enhanced the museum’s digital footprint but also strengthened its connection to the community and beyond. Looking Ahead At Midnet Media, we are proud to have played a part in this transformative project. The Armstrong Air & Space Museum’s new website is just one example of how we strive to elevate cultural institutions through innovative digital solutions. We look forward to continuing our work with the museum and other organizations dedicated to preserving history and fostering education. If your institution is ready to enhance its digital presence, we invite you to reach out to us. Let’s create something remarkable together!